SentinelOne
Supercharging enterprise cybersecurity
After leading their seed funding and supporting every round since, DCVC is excited to back SentinelOne’s $120M Series D as they scale their AI-powered, uniquely resource-efficient endpoint security platform. As evidenced by the recent Crowdstrike IPO and valuation ($12B), the endpoint market is far from over: it has a second wind.
Beyond traditional malware, there are a host of new cybersecurity threats, including ransomware and threats to non-computing devices (IOT). In 2017, high-profile ransomware attacks affected hundreds of thousands of computers across dozens of countries. Cryptojacking—where attackers harness stolen processing power to mine cryptocurrency — burst onto the stage last year, with 8,500% more attacks in 2018 than in the year before.
But personal computers are only part of the story. By 2020, Gartner estimates there will be 20.4 billion “things” in the Internet of Things, 37% of which will operate outside consumer settings. Many of these devices will control critical infrastructure, like water treatment plants and energy grids. Digitalized infrastructure is more efficient, but also more exposed to new, potentially lethal attacks.
In 2019’s Worldwide Threat Assessment, the Director of National Intelligence reminds us that China, Russia, and Iran all have the “ability to launch cyber attacks that cause localized, temporary disruptive effects on critical infrastructure”. Russia has already proven their capability; state-sponsored hackers took down 3 power distribution centers, or oblenegros, in Ukraine in 2015. They left 225,000 people without light or heat, in the dead of winter, for 1 to 6 hours.
Russia has also been charged with infiltrating the U.S. energy grid (as we have theirs), and is a persistent source of malware for monitoring purposes. And, despite Russia’s cyberwar saber-rattling, any U.S. system meeting national requirements could withstand a Ukraine-style attack. (We require two-factor authentication to access control systems, which is something the Ukrainian oblenegros lacked.)
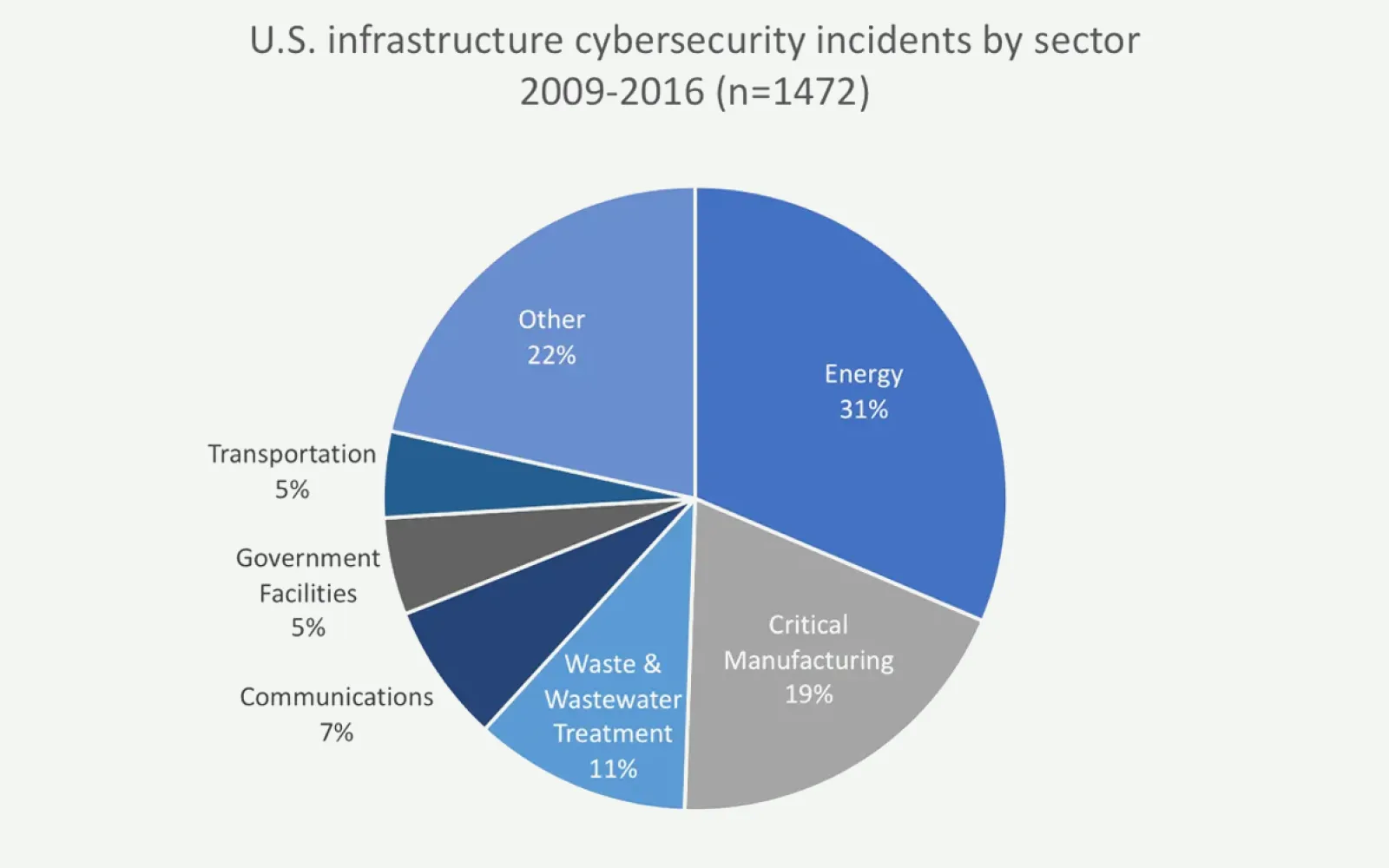
This is not to say our energy system is impervious; in a 2014 survey, “37% of energy sector respondents reported that malware had evaded their defenses” — an uncomfortably large minority. Phishing emails and insecure networks frequently aid these intrusions, including one incident where a hacker compromised an unnamed public power utility and gained access to its control systems.
Energy is not the only sector struggling with the cybersecurity challenge. Much of US industry has been targeted with long-running espionage malware: the Russian Intelligence Service’s Havex program has impacted as many as 2,000 infrastructure sites — across sectors — since its launch in 2010.
Infrastructure is only part of endpoint security’s changing landscape, but the potentially lethal effects of its disruption make it especially critical to protect. While global growth in smartphone and computer ownership drives the number of vulnerable devices, popular new devices, like smart speakers, increase the variety as well. These expand the field of endpoint protection, too. Each new entry point in a network is another possible attack vector: your fitness tracker; your smart bulb; your gaming console.
SentinelOne can protect every device, from industrial control systems to the smart speaker on your counter. Their platform blocks known threats, identifies new ones with AI-driven behavioral analysis, and automatically isolates and halts exploits. They accomplish all of this with software that requires so little memory it can be deployed on even the smallest devices.
In the power grid hack, every part of the system — from the malware-infected computers, to the remotely-accessed workstations on the SCADA system, to the breaker controls themselves — could have been protected by SentinelOne. Their software automatically eliminates new threats, like the malicious industrial control firmware, and disables old ones, like the BlackEnergy or KillDisk malware. By giving its protective software an AI “brain” that catches any exploits it missed, SentinelOne fully combines endpoint protection and endpoint detection and response.
As our environments become more digitized, and as formerly analog machines migrate to the vulnerable Internet of Things, device and data protection become critical for society to function. Most exploits are executed subtly and are only detectable for seconds or minutes. SentinelOne responds to all levels of threat quickly and decisively, without having to pull a human into the loop, without degrading performance, on even the smallest computing footprint. Computer security threats are largely automated — the future of threat protection will be, too. We’re proud to support SentinelOne as they make the digital world a safer place.